tags: windows - malware analysis
Analysis of Sepsis ransomware
Long ago I started writing this report because at that time there was no similar analysis on the Internet. Also I presented it at cybersec meetup 2600 Kazakhstan.
Malware was first discovered on May 14, 2018 by MalwareHunterTeam. I downloaded the sample from Virusshare (you can do it from my repo LINK). Sample has the following hash values:
MD5 1221ac9d607af73c65fd6c62bec3d249
SHA1 518d5a0a8025147b9e29821bccdaf3b42c0d01db
SHA256 3c7d9ecd35b21a2a8fac7cce4fdb3e11c1950d5a02a0c0b369f4082acf00bf9a
The analysis was carried out on Windows 7 Ultimate SP1 64-bit. The main purpose was not only find out what malware does but also HOW it commits malicious actions. The type of malware is a ransomware. Launch damage can be seen on the screenshot.
All files are encrypted and [Sepsis@protonmail.com].SEPSIS have been added to their names. Windows VM crashed.
Static analysis.
First of all, open the file in PPEE with FileInfo plugin.
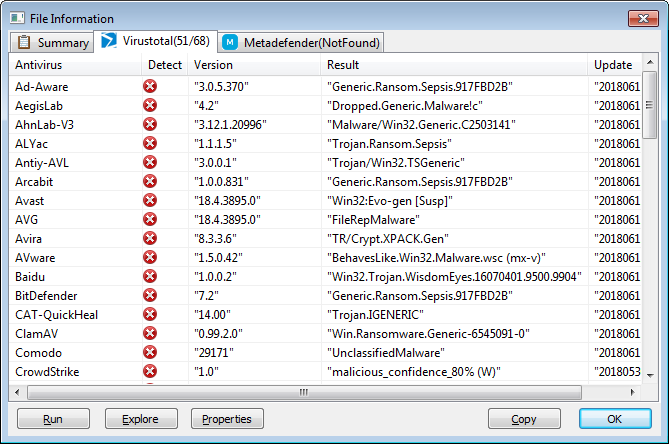
As we see, 51 out of 68 antiviruses define a file as malicious. Let’s move on to suspicious strings.
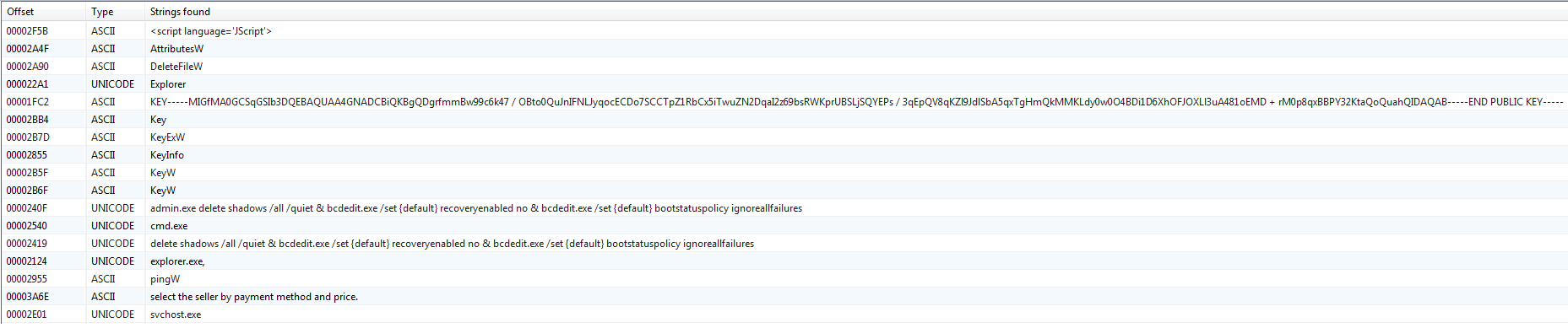
Look at the line -KEY- … - END PUBLIC KEY- - this is the public key that most likely encrypts data.
The line looks like an argument to cmd.exe:
admin.exe delete shadows /all /quiet & bcdedit.exe /set {default} recoveryenabled no & bcdedit.exe /set {default} bootstatuspolicy ignoreallfailures
admin.exe delete shadows /all /quiet - deletes all backups of the system to prevent the recovery of damaged files.
bcdedit.exe /set {default} recoveryenabled no - disables recovery mode.
bcdedit.exe /set {default} bootstatuspolicy ignoreallfailures - disables the appearance of the Windows Error Recovery screen.
Open the URL strings.
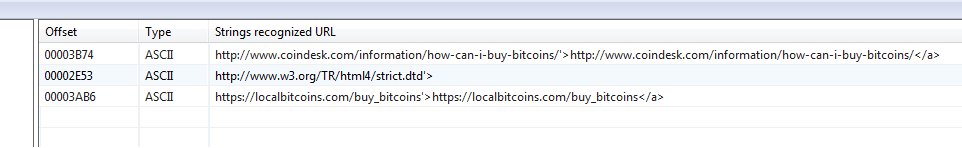
By line
http://www.coindesk.com/information/how-can-i-buy-bitcoins/'>http://www.coindesk.com/information/how-can-i-buy-bitcoins/</a >
it can be understood that the user will be asked to bitcoins and give a link to how to do it.
Open the Registry strings.
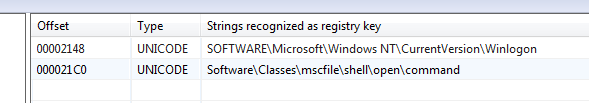
Pay attention to Software\Classes\mscfile\shell\open\command. The registry branch Software\Classes contains information about which programs are responsible for handling certain file types. That is, the malware most likely adds some commands that will be executed every time you open the .msc file. It is possible that malware affects the operation of the Winlogon process, which is responsible for logging in/out of the system.
PE headers are normal.
No more interesting PPEE shows. You should not hope to receive complete information using PPEE or other utilities, but for obtaining initial information and information about what a file is, this may be enough. Strings can be added specifically to confuse or recover dynamically or to be encrypted. Strings in the file can also be viewed using the famous strings program, but its more powerful counterpart is FLOSS from FireEye. It can show even obfuscated strings in a binary.
We launch it with a command with writing to a file since it has a very large output.
floss sepsis.bin > c:\floss_output.txt
Open and browse the resulting file. We can see html file with such content.
`<body>`
`<div class='header'>`
`<div style='color:yellow'>Welcome to Sepsis Ransomware!</div>`
`<div style='color:blue'>All your files have been encrypted!</div>`
`</div>`
`<div class='bold'>All your files have been encrypted due to a security problem with your PC. If you want to restore them, write us to the e-mail <span class='mark'>Sepsis@protonmail.com</span></div> <div class='bold'>Write this ID in the title of your message <span class='mark'>16E734E0</span></div>`
`<div class='bold'>In case of no answer in 24 hours write us to theese e-mails:<span class='mark'>sepsis@airmail.cc</span></div>`
`<div>`
`The price depends on how fast you write to us. You have to pay for decryption in Bitcoins. After payment we will send you the decryption tool that will decrypt all your files.`
`</div>`
`<div class='note info'>`
`<div class='title'>Free decryption as guarantee</div>`
`<ul>Before paying you can send us up to 5 files for free decryption. The total size of files must be less than 10Mb (non archived), and files should not contain valuable information. (databases,backups, large excel sheets, etc.) </ul>`
`</div>`
`<div class='note info'>`
`<div class='title'>How to obtain Bitcoins</div>`
`<ul>`
`The easiest way to buy bitcoins is LocalBitcoins site. You have to register, click 'Buy bitcoins', and select the seller by payment method and price. `
`<br><a href='https://localbitcoins.com/buy_bitcoins'>https://localbitcoins.com/buy_bitcoins</a>`
`<br> Also you can find other places to buy Bitcoins and beginners guide here:`
`<br><a href='http://www.coindesk.com/information/how-can-i-buy-bitcoins/'>http://www.coindesk.com/information/how-can-i-buy-bitcoins/</a>`
`</ul>`
`</div>`
`<div class='note alert'>`
`<div class='title'>Attention!</div>`
`<ul>`
`<li>Do not rename encrypted files.</li>`
`<li>Do not try to decrypt your data using third party software, it may cause permanent data loss.</li>`
`<li>Decryption of your files with the help of third parties may cause increased price (they add their fee to our) or you can become a victim of a scam.</li>`
`</ul>`
`</div>`
`</body>`
It looks like a message that will be shown to the victim after encrypting the files. We also see the line SeDebugPrivilege, which means that malware may connects to other processes. The line eventvwr.exe, in resulting output - signals a possible attempt to raise privileges. We also see names similar to the list of folders:
Windows
MSOCache
Perflogs
DVD Maker
Internet Explorer
Reference Assemblies
Windows Defender
Windows Mail
Windows Media Player
Windows NT
Windows Sidebar
Startup
Temp
Program Files
Program Files (x86)
They probably used as a blacklist when encrypting.
Open the file in PEiD to find out if packers have been used.
DIE shows us that the program is written in C/C++, this will allow us to decompile it well with HexRays in IDA.
You can guess what malware does without starting it by examining the imported libraries and their functions. This may not always help, as the file can be packed, but in our case we are lucky.
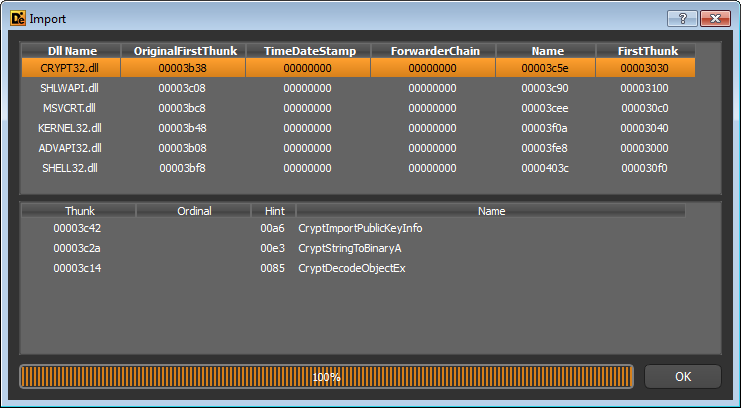
crypt32.dll for encryption, advapi32.dll working with the registry.
Dynamic analysis.
The logic of the work of Sepsis in pseudocode.
1 if (elevated)
2 copy_to(C:\Windows\svchost.exe)
3 add_to_autorun()
4 exec(C:\Windows\svchost.exe)
5 sleep()
6 else
7 copy_to(%TEMP%\svchost.exe)
8 add_to_autorun()
9 if (!elevated)
10 run_as_elevated()
11 sleep()
12 if (run_first)
13 run_first = FALSE
14 else
15 exit()
16 encrypt_all_data()
17 if (elevated)
18 wipe_backups()
19 set_process_critical()
20 rename_all_files()
21 show_user_manual()
22 exit()
As we can see, the malware checks whether it is launched with elevated privileges - lines 1, 9, 17. Checking with TokenInformation, after calling GetTokenInformation, with the TokenElevation parameter.
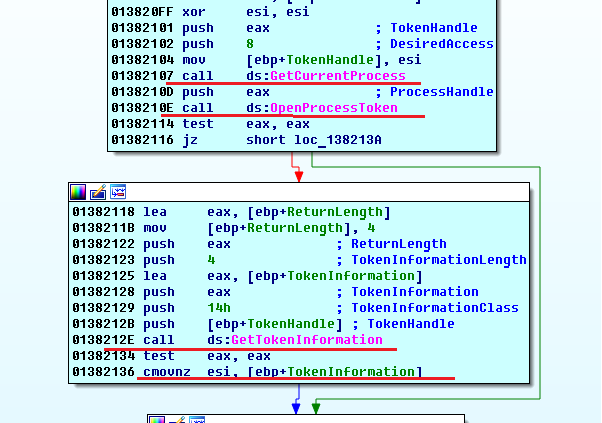
The first launch on the victim’s computer is assumed without elevated privileges so the malware copies itself to a temporary folder (line 7), under the name svchost.exe


and adds itself to autorun (line 8) by adding %TEMP%\svchost.exe to the HKCU\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\Shell.

Winlogon is the process responsible for the session of the OS user (provide logging in and logging out of the system). When booting the OS, Winlogon starts what is written in the Shell key, that’s why the malware is launched.
In line 9, again there is a check for the presence of elevated rights and if it’s not true, then the malware makes privilege escalation (line 10). How does malware do it? This is done by adding to the registry branch HKCU\\Software\\Classes\\mscfile\\shell\\open\\command. All that is written to this registry branch will be launched when opening files of type .msc. Next, malware runs eventvwr.exe - a Windows system utility that runs the Microsoft Management Console (mmc.exe), which immediately loads the .msc file. The magic is that eventvwr.exe is compiled with autoElevated = True in the manifest, which allows it to run with elevated rights bypassing UAC and not showing the user a window requiring consent to run. Thus, Sepsis launches itself SECOND time. In line 11, the malware falls asleep and the second instance comes into play. The first instance, after hibernation and checking in line 12, stops in line 15. The check for restart occurs by creating a mutex with the unique name HJG> <JkFWYIguiohgt89573gujhuy78 ^ * (& (^ & ^ $ and checking the availability for opening.

Now, we will analyze the work of malware after restart. As we see, the first launch was necessary to add to autorun and launch itself with elevated rights. After running in elevated rights, the malware brazenly copies itself to C:\Windows\svchost.exe, without generating any pop-up windows.

As we can see, after running CopyFile, the file C:\Windows\svchost.exe has the same hash as the original file.

Line 16 encrypts all files, except files in folders:
Windows
MSOCache
Perflogs
DVD Maker
Internet Explorer
Reference Assemblies
Windows Defender
Windows Mail
Windows Media Player
Windows NT
Windows Sidebar
Startup
Temp
Program Files
Program Files (x86)
The public keys (that we saw in previous static analysis) was imported

Files are encrypted using the CryptEncrypt function.

Line 18 deletes all existing backups, using the command we saw earlier -
/c vssadmin.exe delete shadows /all /quiet & bcdedit.exe /set {default} recoveryenabled no & bcdedit.exe /set {default} bootstatuspolicy ignoreallfailures.
This is done so that the user cannot recover the encrypted files.
Line 19, by calling the RtlSetProcessIsCritical undocumented function, the main process of Sepsis become system process. When the malware completes its work it completes its process and since it is system process OS crashes and reboots.
Line 20, for each existing disk in the system, an additional thread is created that renames all files in each folder with the exception of the list above.
Line 21, a file with html content (that we saw earlier) is created and displayed to the user.
System Restore & IOC
Delete files %TEMP%\svchost.exe, C:\Windows\svchost.exe
A unique pattern of malware sample is the name of the mutex
"HJG> <JkFWYIguiohgt89573gujhuy78 ^ * (& (^ & ^ $"