tags: windows - malware analysis
Analysis of trojan
One day I asked to analyze suspicious file named FirefoxUpdate.exe. It has hash value:
MD5: 342E134B3DE901EE6A915909AECDAC4A
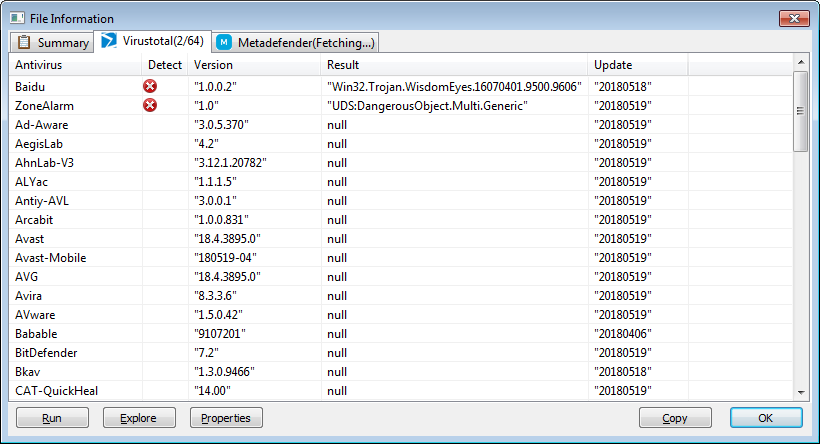
EXE is not packed, written in C#. Two AV on Virustotal define it as Win32.Trojan.WisdomEyes and UDS: DangerousObject.Multi.Generic.
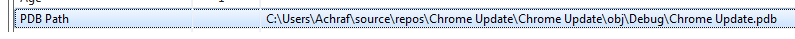
By examining pdb data inside file we can conclude that the user name on the developer’s computer is Achraf
After decompiling the file, we can see that at startup, the page at http://164.132.197.47/security-updates/available.php is downloaded.
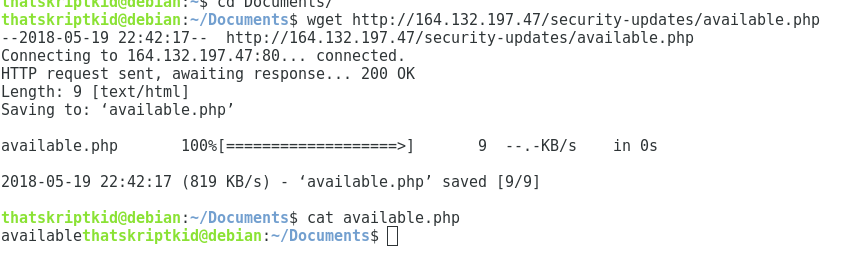
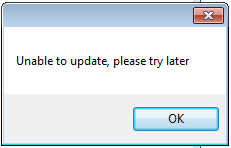
If the page contains the string “available”, then malware can start to work. Otherwise, a window is displayed with the text “Unable to update, please try later”
Next, exe creates a folder C:/Program Files/ChromeUpdates/. Depending whether the OS is 32- or 64-bit, this number is added to the address http://164.132.197.47/security-updates/. Three files are downloaded from resulting link: update.exe, config.json, ChromePassBackup.exe. Files are saved in the folder C:/Program Files/ChromeUpdates/.
Contents of the config.json file:
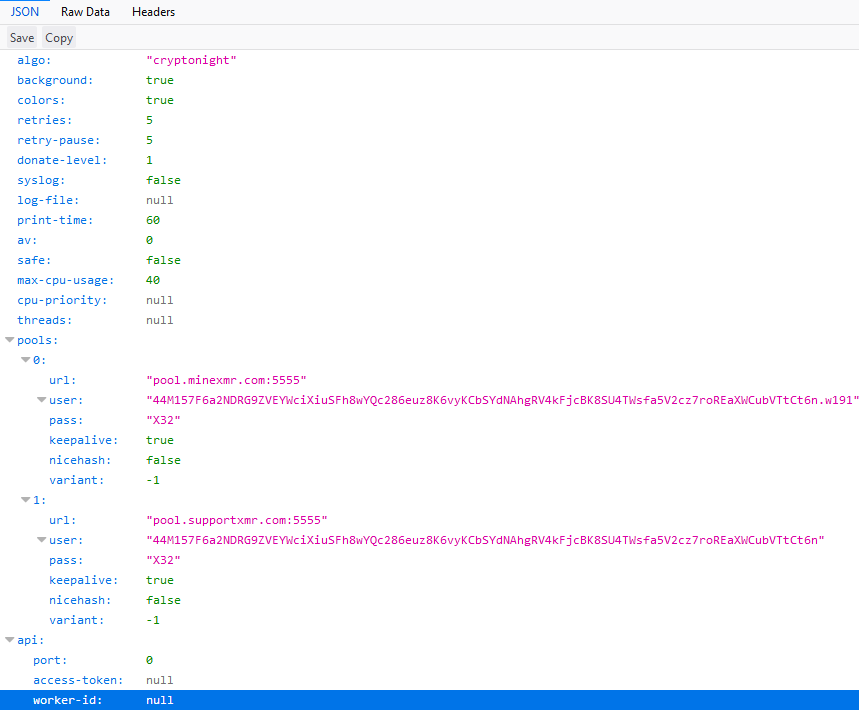
URLs tell us that this is Monero miner’s config.
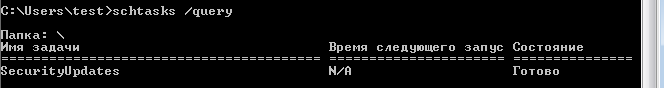
At the end of the download, a new cmd.exe process is created with a hidden window with the following arguments - /C schtasks /create /tn SecurityUpdates /tr "C:\Program Files\ChromeUpdates\update.exe" /sc onstart /RU SYSTEM.
From the command line, schtasks.exe is launched. This program creates (/create) a scheduled task with the name (/tn) SecurityUpdate, which will launch (/tr) the file C:\Program Files\ChromeUpdates\update.exe, at the start systems (/sc onstart) using the user SYSTEM (/RU SYSTEM).
Next, a string is generated that is 12 characters long, consisting of random characters picked from string abcdefghijklmnopqrstuvwxyz0123456789.
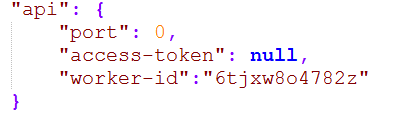
This string is substituted for NULL in worker-id field in the file C:\Program Files\ChromeUpdates\config.json. Looks like a random token for mining client.
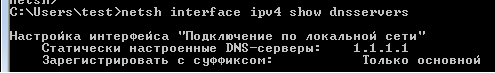
Next, a new cmd.exe process is created with the arguments /C netsh interface ipv4 add dnsservers
NAME_OF_NONLOCAL_NETWORK_INTERFACE address = 1.1.1.1 index = 1. This adds 1.1.1.1 on top of the dns list to all available network interfaces, except for Loopback.
At the end of the process, the Update complete window appears.
ChromePassBackup.exe
The exe downloaded in the previous step is a utility for viewing passwords saved in Google Chrome nirsoft.
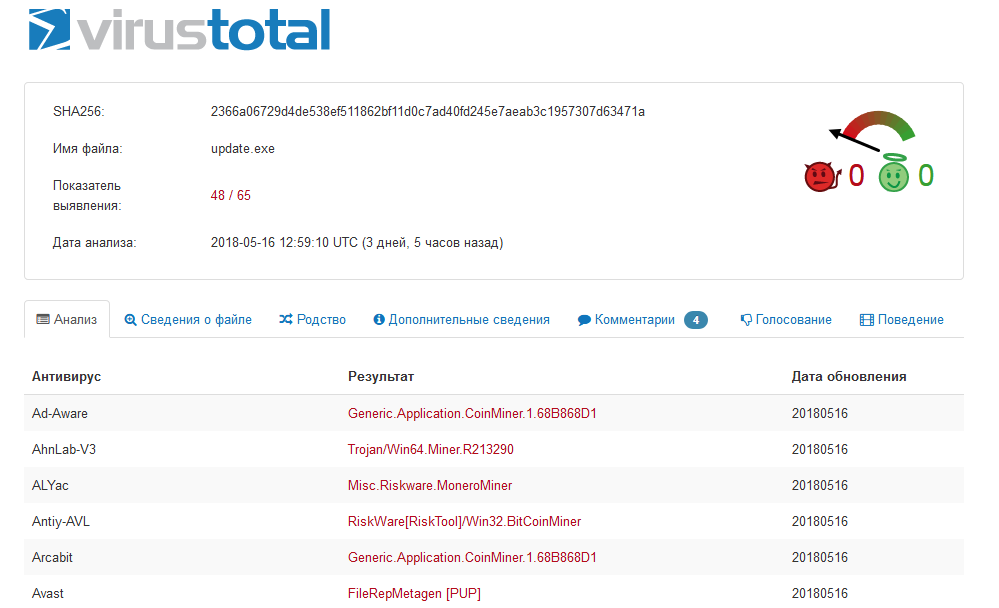
Update.exe
This file was scheduled. Virustotal defines the file as a miner. Miner repository: https://github.com/xmrig/xmrig/releases
System Restore & IOC
1) Delete the folder C:/Program Files/ChromeUpdates/
2) Block ip hxxp://164(.)132(.)197(.)47/ in the firewall
3) Delete the scheduled SecurityUpdate task with the command:
schtasks /Delete /TN SecurityUpdate
4) Change the DNS server to the desired, instead of 1.1.1.1
Вверх